
The saying “You’re only as strong as your weakest link” has never been more relevant as organizations increasingly lean on third parties for various services. Today, building cyber resilience isn’t just about securing your internal systems, it’s also about assuring that your vendors, partners, and service providers are securing their systems, too. This is especially crucial when you realize that a whopping 98% of organizations do business with a third party that has experienced a security breach.
98% of organizations do business with a third party that has experienced a security breach
Fortunately, when executed effectively, third-party security risk assessments can empower information security & assurance teams and their organizations during the procurement process. These assessments proactively mitigate third-party risks and help foster transparent, compliant, and collaborative relationships with third parties and the broader organization.
This Complete Guide from SaltyCloud dives into third-party security assessments. It provides a clear definition, explains its importance, and walks you through the entire process—from initial planning and key risk identification activities to in-depth analysis and final attestation. Ultimately, this guide equips you with the knowledge and tools to conduct a practical, effective third-party security risk assessment as a fundamental component of your Third-Party Security Risk Management (TPSRM) program.
A third-party security risk assessment is a comprehensive evaluation of a third party’s security posture, whether a vendor, partner, client, contractor, consultant, or intermediary. The goal is to ensure their security practices meet your organization’s minimum security standards.
Third-party security risk assessments are due diligence exercises where information security & assurance teams inventory third parties and conduct various risk identification activities. These activities may include specialized security questionnaires, real-time risk intelligence feeds, penetration tests, vulnerability scans, certification reviews, and detailed internal policy examinations. All these efforts aim to identify the third party’s deficiencies and ensure compliance with minimum security standards and regulatory requirements.
Third-party security assessments are due diligence exercises where information security & assurance teams inventory third parties and conduct various risk identification activities.
The results of these activities are vital in facilitating open communication among all stakeholders. They bring everyone together to discuss findings, have transparent conversations with third parties, and determine the course of action if risks are identified. The third-party risk owners must decide whether to accept the risk, create an addendum with the third party, or reject the third party altogether.
In an era where cyber threats constantly evolve, the question is not “if” but “when” a security incident will occur. Yet, according to a recent study, 54% of businesses do not vet third-party vendors properly. Your organization may have implemented robust internal security controls, but can the same be said about your third-party vendors?
According to a recent study, 54% of businesses do not vet third-party vendors properly
Here are some of the key reasons these assessments are indispensable:
One of the most immediate and alarming concerns is the increasing frequency of supply chain attacks. In these incidents, adversaries exploit vulnerabilities in one organization to compromise a larger network of associated companies. For example, a minor breach in a third-party vendor with limited security controls can lead to unauthorized access to your ecosystem, putting sensitive data and systems at risk. According to a 2023 study, although 84% of businesses claim to prioritize third-party risk management, more than 40% have insufficient visibility into their digital supply chain. Third-party security risk assessments are a proactive solution to identify and mitigate such vulnerabilities before putting your trust in a third-party vendor.
Regulatory compliance is another major factor driving the need for third-party security assessments. Laws and standards like GDPR, HIPAA, GLBA, CMMC, PCI-DSS, and others include specific clauses holding organizations accountable for protecting regulated data with third-party vendors. Non-compliance can result in hefty fines, legal repercussions, and reputational damage. Conducting regular third-party security risk assessments helps not only maintain compliance but also demonstrate due diligence to auditors and stakeholders.
A vendor-related security incident can have a domino effect, disrupting your operations and affecting business continuity. But in 2023, it took an average of 277 days to identify and contain a breach. Assessments help evaluate your vendors’ resilience against cyberattacks before they occur. This information is vital for your own business continuity planning and can be particularly useful in industries where uptime and data integrity are critical.
Third-party security risk assessments offer an empirical basis to hold your vendors accountable. By evaluating a vendor against predefined metrics and security controls, you can ensure they meet industry standards. This is especially crucial during onboarding new vendors and periodic review of existing partnerships.
Understanding the security posture of third-party vendors helps assess the level of risk they pose to your organization. This enables more informed decision-making, whether you are contemplating entering into a new business relationship or considering the renewal of an existing one. Your findings may lead to constructive dialogues with vendors about possible remediation measures or cybersecurity improvements.
Third-party security risk assessments are an optional best practice and a critical component of modern information security strategy. Given the current landscape of cyber threats, data breaches, regulatory demands, and interconnected business ecosystems, these assessments offer a critical line of defense against third-party security risks.
Third-party security risk management software, usually a part of a broader governance, risk, and compliance (GRC) platform, offers tools that enhance and automate the third-party security risk management (TPSRM) process. However, most of these solutions often introduce more complexities than they solve.
Isora GRC offers a solution for TPSRM, with the features to inventory your third-party ecosystem, launch and manage questionnaire-based assessments, collect and securely store evidence, produce vendor scorecards and reports, and manage and assign risks in a risk register.
Isora is a collaborative GRC platform that empowers everyone to own risk together, with user-friendly and flexible tools. With Isora, teams can stay agile and responsive to growing changes, fostering a resilient culture across the organization.
In the “Conduct the Assessment” section of this Complete Guide, we’ll demonstrate how Isora helps at each step of your third-party security risk assessment.
Conducting a third-party security risk assessment is a critical, ongoing process. Establishing clear guidelines through formal policies is important, ensuring a standardized approach across all assessments. This foundational planning prevents starting from scratch with each assessment and embeds a structured methodology into your team’s practices.
As you prepare for an assessment, consider these key policy elements:
Clearly delineate the duties of everyone involved, from your internal teams to external vendors, and set up a clear reporting hierarchy. Align these roles with your organization’s broader goals to ensure focused accountability and strategic cohesion.
Here are some key players to identify:
Incorporate your data classification framework to enforce security measures across third-party interactions uniformly. Categorize data into tiers such as Public, Internal Use Only, Confidential, and Highly Confidential, each with tailored security protocols. For example, while Public data may require minimal protection, Highly Confidential data demands robust encryption and strict access controls.
It’s crucial to consider regulated data within these classifications. Data subject to legal and regulatory mandates, such as Personally Identifiable Information (PII), Protected Health Information (PHI), or financial data governed by regulations like GDPR, HIPAA, or PCI-DSS, requires specific handling and protection measures. These requirements should be integrated into the security protocols for the relevant classification levels.
Regular reviews of these classifications and their security measures are essential to remain compliant with evolving legal frameworks and to mitigate new risks. This dynamic approach to data classification and protection ensures the security of sensitive and regulated data and enables your information security risk management strategy.
Tailor the evidence collection for your assessments to match the unique aspects of each third-party engagement, taking into account the type of interaction, the data at stake, and the associated risks. Information security teams can generally consider the following:
It’s important to note that seeking evidence from various sources is recommended for a more robust risk assessment. A multi-faceted evidence approach improves the confidence of your assessments and contributes to a well-rounded view of the third party’s security practices and compliance status.
Finally, to tie it all together, a well-constructed rubric can be a valuable tool to help your organization align with the requirements. This rubric can blend the data classification protocols and evidentiary requirements with your organization’s regulatory obligations and internal security standards. It provides a cohesive set of criteria that helps guide and measure the effectiveness of your assessments.
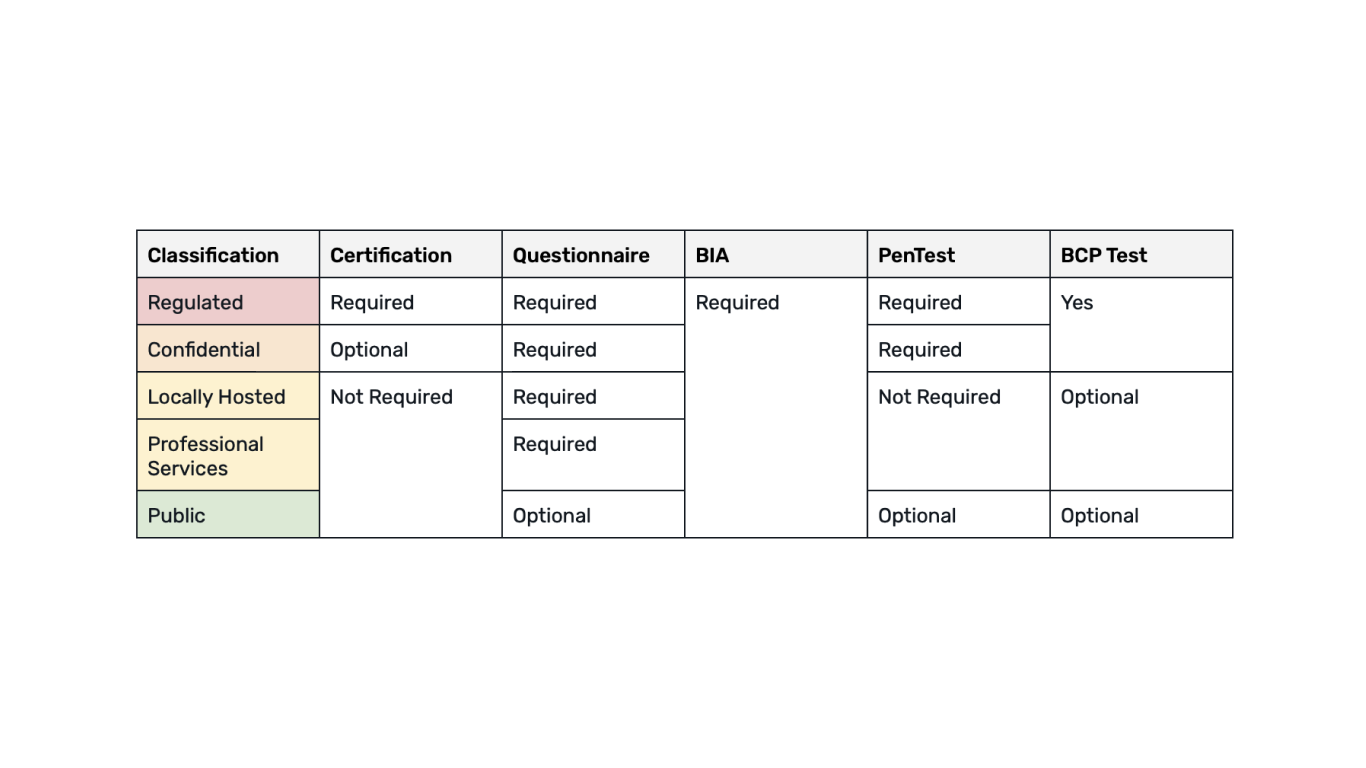
A simple example of a third-party security risk assessment requirement rubric where a series of data classifications are tied to a series of evidentiary requirements.
Engaging in a third-party security risk assessment involves a series of interconnected steps that are integral to the risk management cycle. This process ensures that every phase—risk identification, risk analysis, and risk evaluation—is carried out cohesively and contributes to a comprehensive understanding of potential security risks.
By conducting an assessment, it means you are actively managing and executing a strategic sequence of events that begins with identifying risks and culminates in their thorough evaluation. Historically managed with spreadsheets, email threads, and shared drives, this process has evolved with a platform like Isora, which intuitively organizes and centralizes the process.
The first step in conducting a third-party security risk assessment is to set clear objectives, define the necessary evidence, and establish a timeline with due dates for completion.
When using Isora, the assessment begins with the third-party vendor assessment wizard. This feature helps you quickly and effectively organize all the details of your assessment into an interactive survey. This includes entering comprehensive details about the vendor and product, assigning the business unit and team responsible for the assessment, and giving the assessment a descriptive name, such as “Initial Security Evaluation.” You can also group assessments by similar data classification categories to create a series, which helps manage and compare assessments systematically.
Setting a due date for automated email reminders ensures timely responses, and with Isora, you can provide clear, structured instructions to participants. This is made possible by using markdown language, allowing you to add headers, links, and images, enhancing engagement and clarity.
Furthermore, you can select a questionnaire template that aligns with popular security frameworks from Isora’s preloaded options, or you may create a custom template to fit your assessment criteria better.
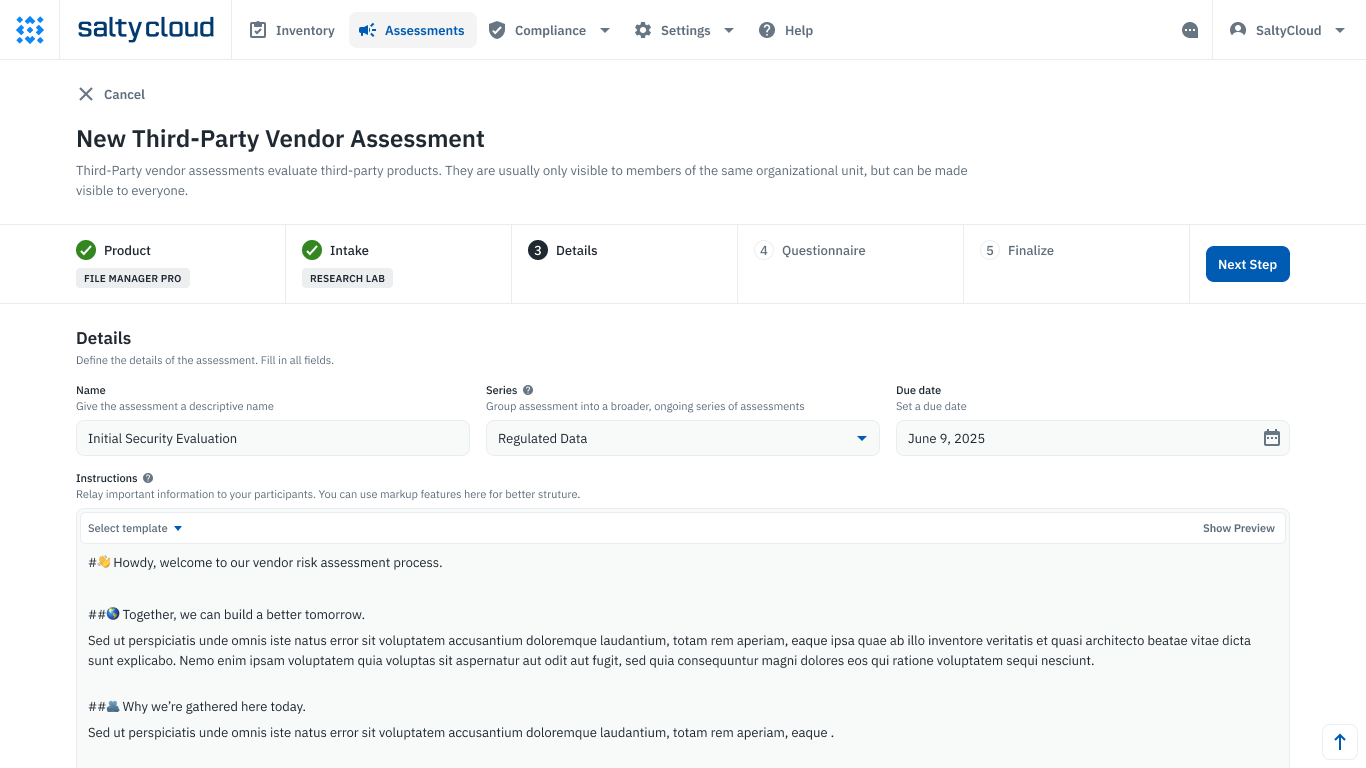
The third-party vendor assessment wizard screen on Isora.
Once the assessment is launched, Isora’s central assessment management dashboard allows you to track all your third-party assessments, views details at-a-glance, access the survey, and ultimately review the vendor scorecard and report upon completion.
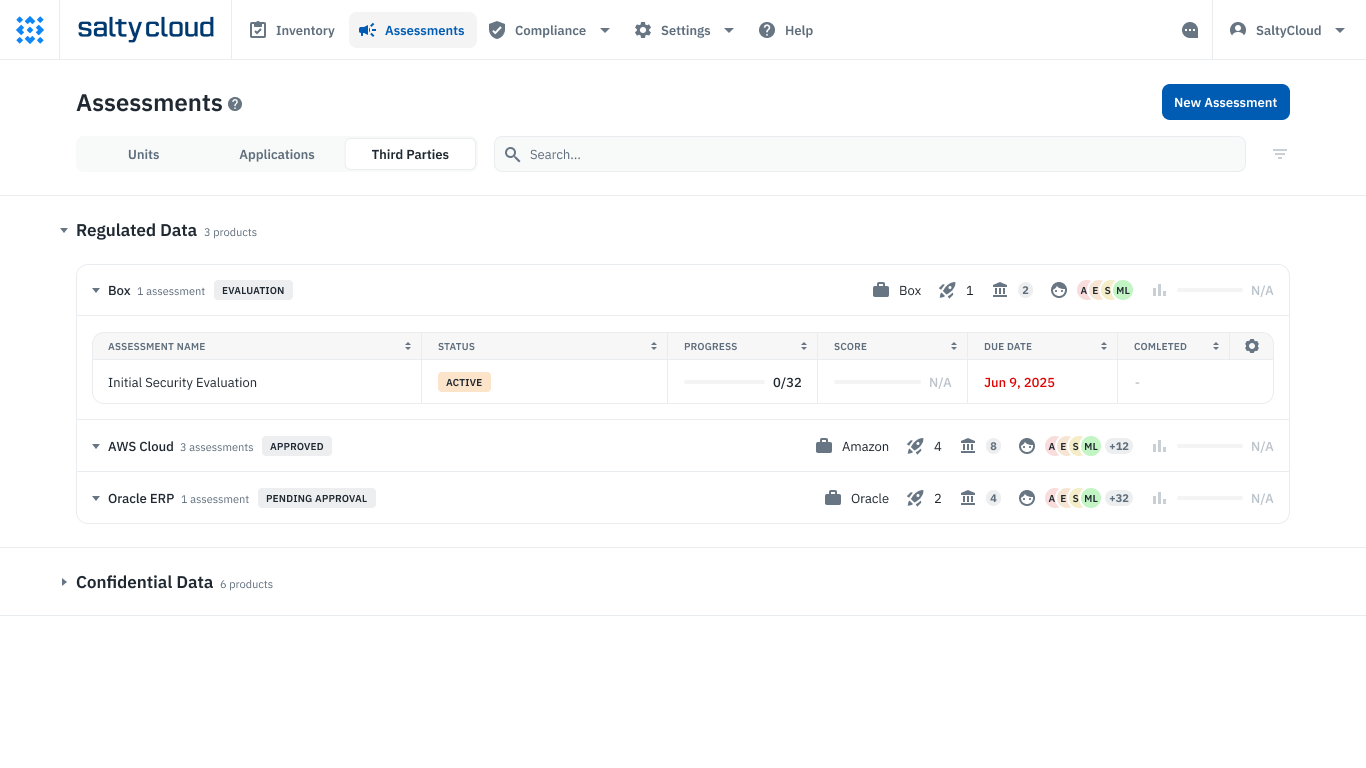
The third-party vendor assessment management dashboard on Isora.
Progressing to the next critical phase of the third-party security risk assessment requires the collection of detailed information and supporting evidence from your vendor contacts. This stage is designed to align with your organization’s security requirements, which may include deploying a structured questionnaire informed by established frameworks like SIG, CAIQ, or HECVAT, alongside additional questions that are specific to your organizational context.
When utilizing Isora for this process, third-party vendors are granted access to a distinct survey page that houses the questionnaire tailored to their evaluation. Isora enhances this experience by allowing for the construction of questionnaires with bespoke logic, where questions can have customized answer choices and the capability to prompt follow-up questions based on previous responses. Open-text fields are available for vendors to provide additional context to their answers, and there is the functionality to attach documents directly to questions, offering a secure method for vendors to furnish supplementary details.
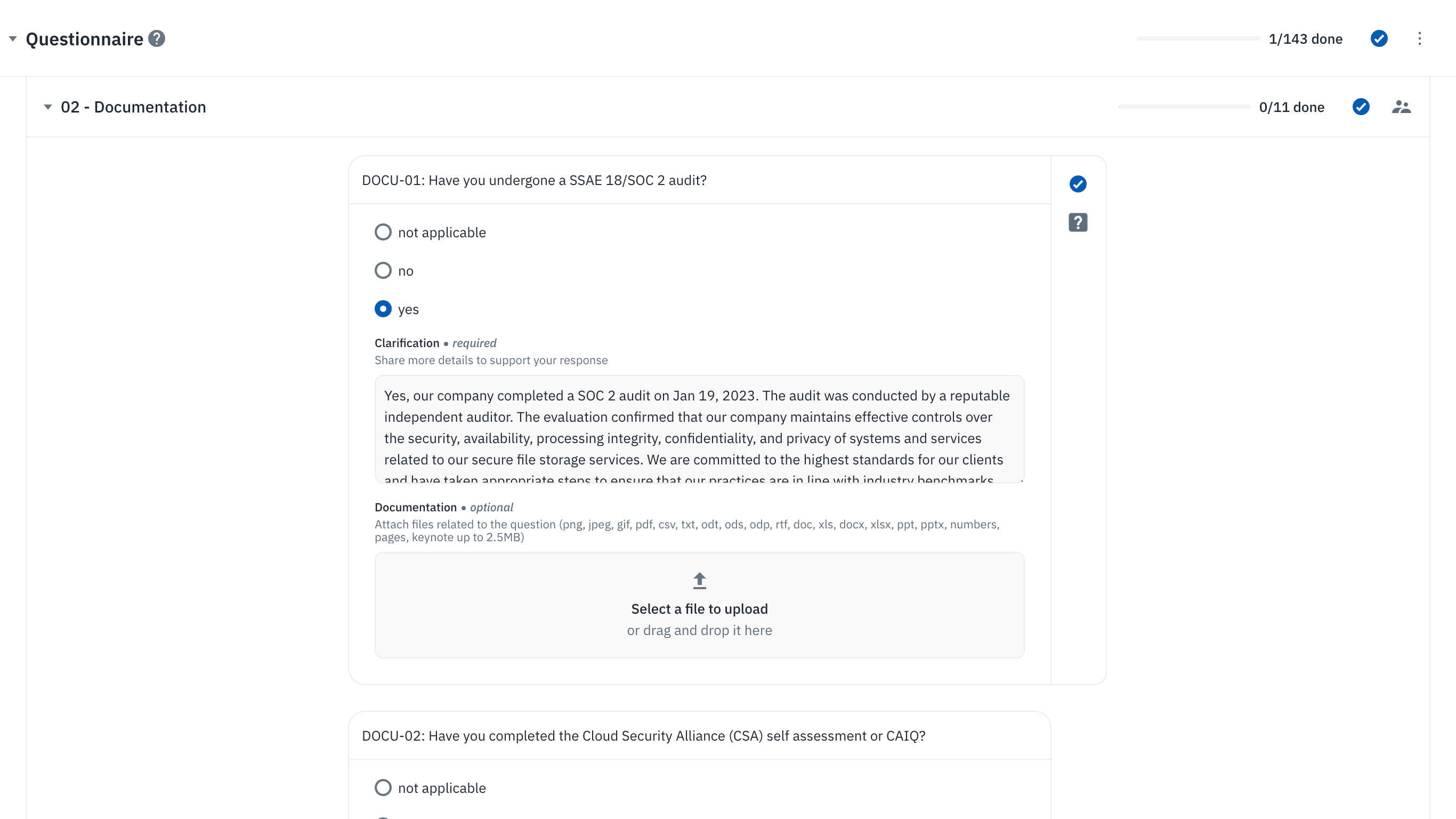
The survey experience for external third-party vendor contacts on Isora.
Each question within the survey can be augmented with help text, providing clear guidance to the vendor on what information is required and the purpose behind each query. This rich questionnaire environment cultivated by Isora is pivotal in moving away from the traditional spreadsheet-based questionnaires, extensive email exchanges, and fragmented evidence collection. It consolidates all pertinent information into one centralized location. This not only simplifies the information gathering process but also ensures that it’s comprehensive. Since it’s typical for responses to come from different stakeholders within the third-party vendor’s team, the survey link can be shared across their internal teams, facilitating a seamless and collaborative collection of evidence.
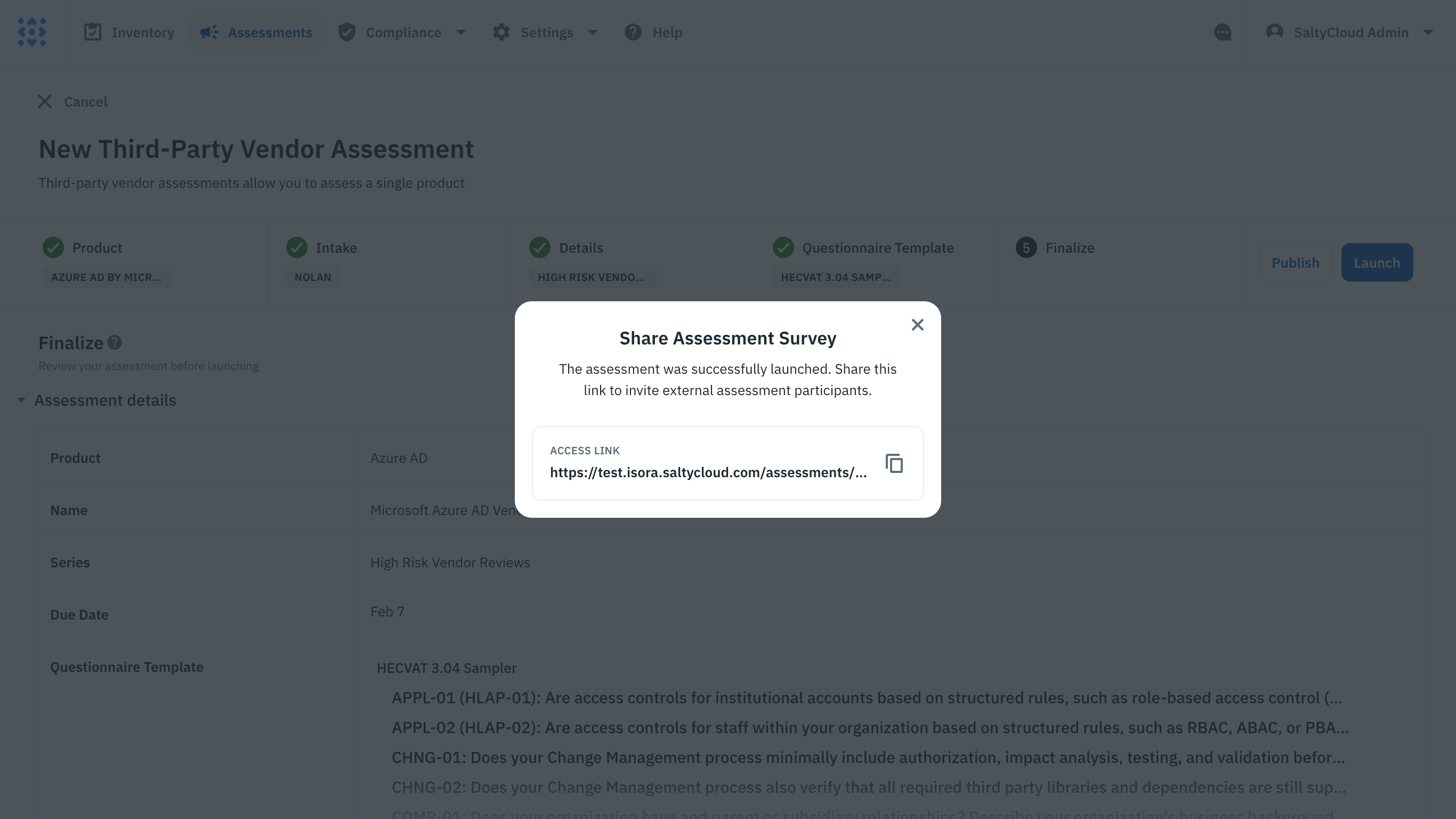
The shareable survey link on Isora.
After all the necessary details and evidence have been gathered, the next crucial step is to secure a signed attestation from your third-party vendor. This is where the vendor affirms the accuracy and relevance of the information they’ve submitted as part of the assessment. It’s a declaration that all provided data is factual and relevant to the security evaluation being conducted.
In Isora, this process is made straightforward. Upon marking all questions as complete, the vendor contact can submit the survey where they are prompted to attest to the information provided. This involves entering their name, email, job title, and phone number, and agreeing to a statement that verifies the truthfulness of their responses.
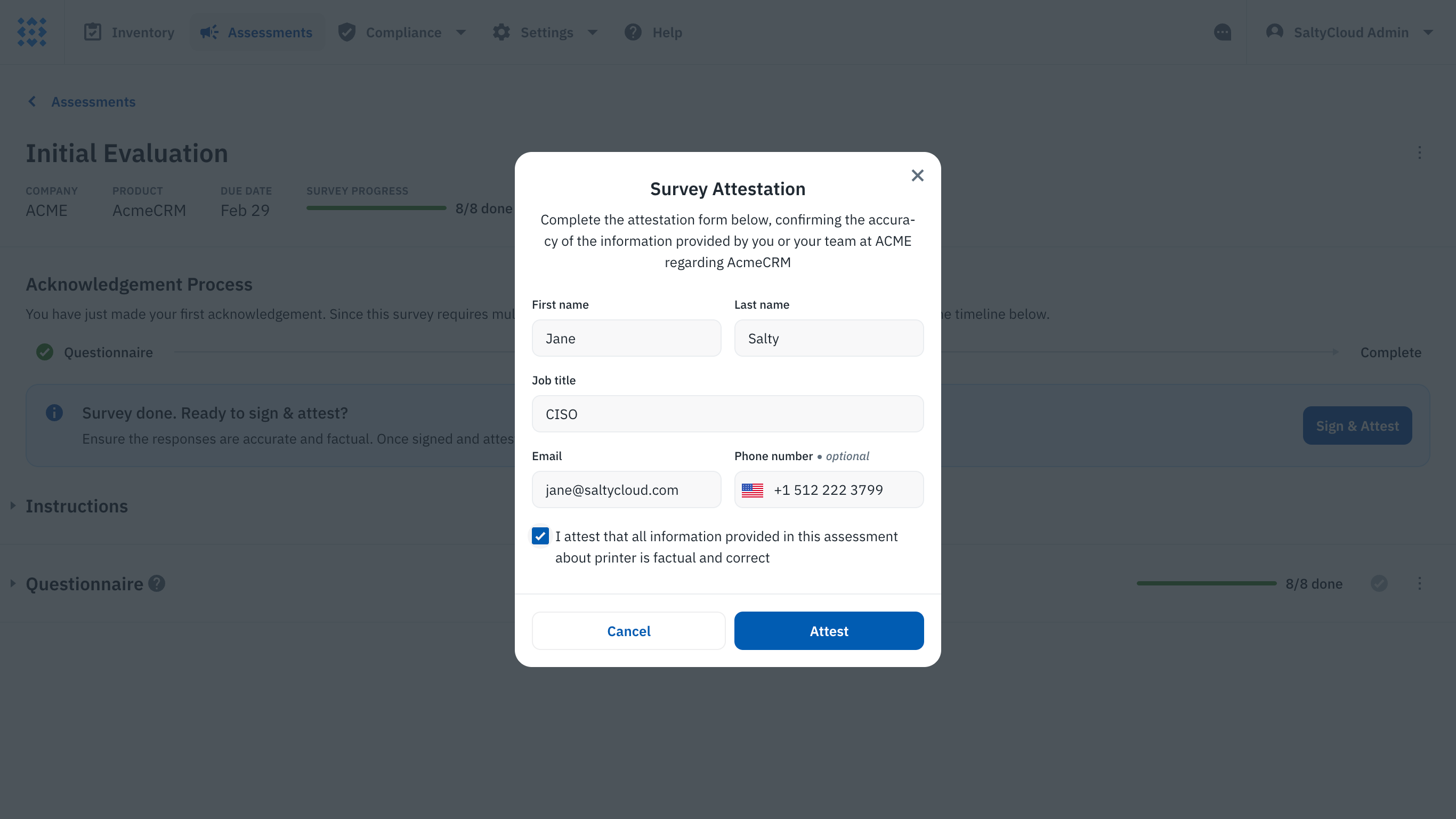
The attestation section of a third-party questionnaire on Isora.
This attestation is not just a formality—it plays a critical role in the assessment process. The act of attesting formalizes the vendor’s accountability for the provided information. After the attestation is completed all responses are securely saved and the attestation contact details are stored within the system, which is vital for any future audits, ensuring that there is a clear trail of accountability.
For added transparency and record-keeping, the vendor also has the option to download a CSV file of their responses, allowing them to retain a copy for their records.
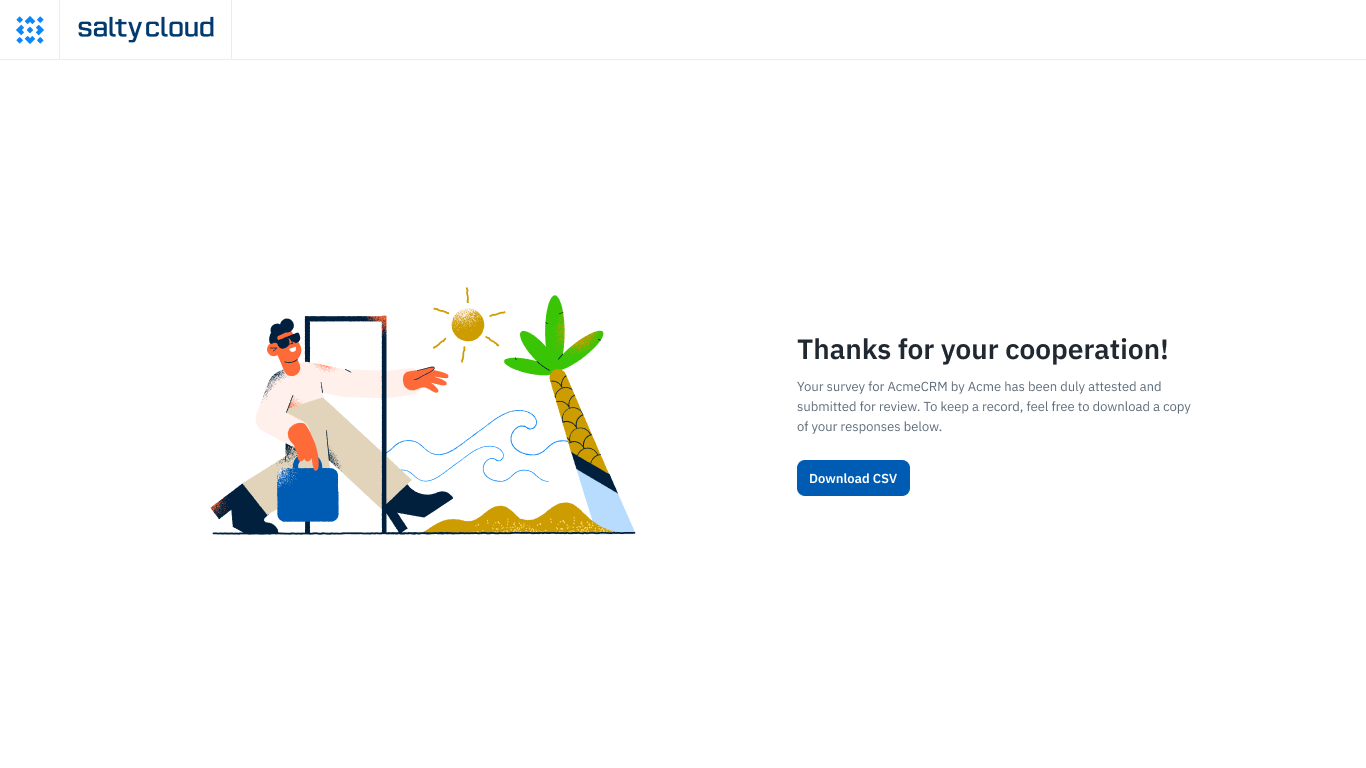
The screen a third-party vendor contact sees when they’ve completed their questionnaire on Isora.
The concluding phase of the assessment process is perhaps the most critical, as it involves the meticulous task of identifying, analyzing, and evaluating potential risks based on the details and evidence collected from your third-party vendor. This stage often requires the most diligence, as you go through all the evidence with great attention to detail to ensure no stone is left unturned.
With Isora, this crucial step becomes organized and efficient. After the external contact submits their completed survey, Isora automatically scores the responses and arranges all evidence for your review. The platform provides an array of widgets for a quick overview, including scores for the overall questionnaire and by each question category. This immediate visualization allows for a rapid assessment of areas where responses were less than favorable, prompting a closer review.
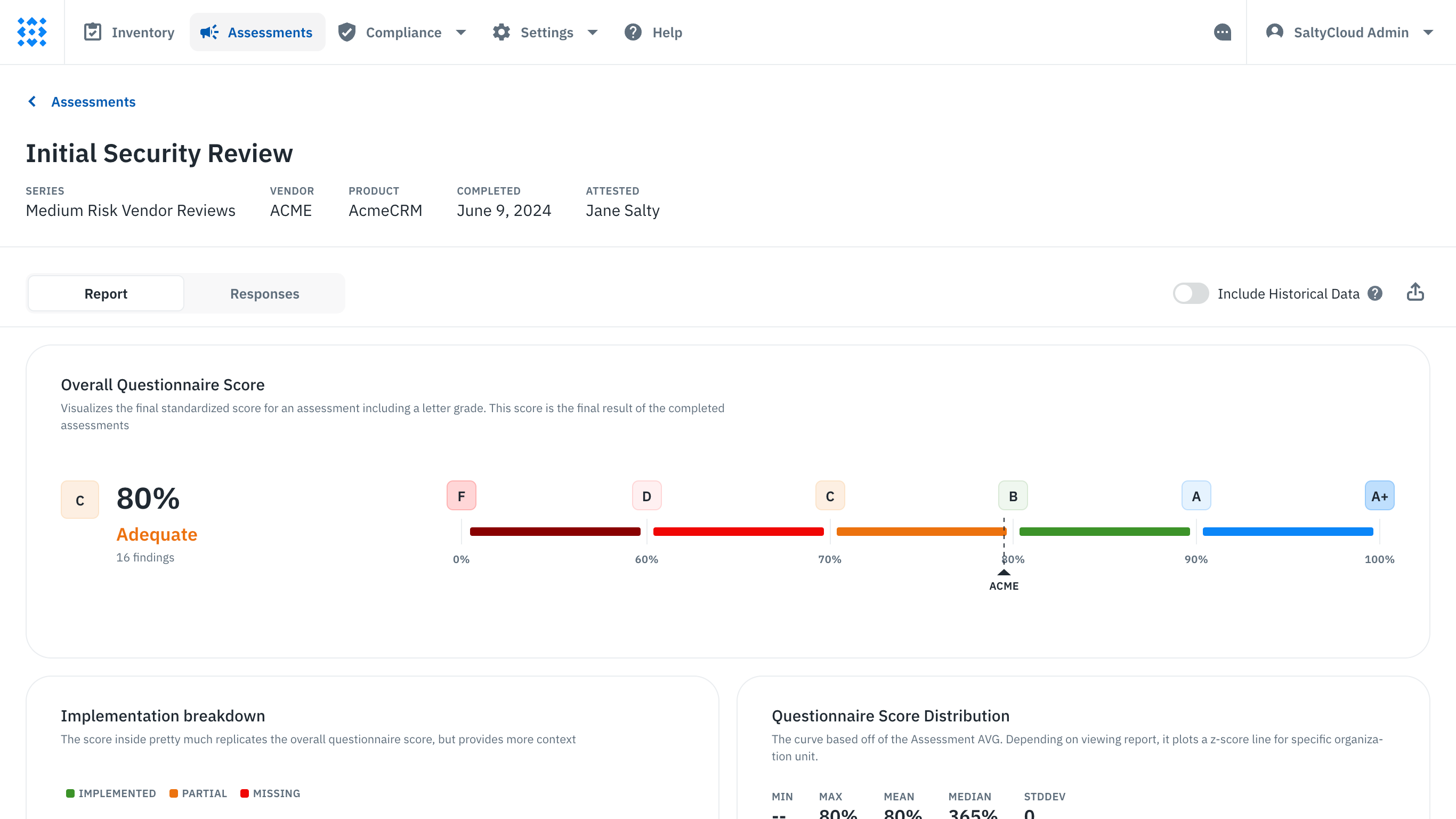
The third-party vendor scorecard report on Isora.
You can then delve deeper into individual responses and analyze the vendor’s clarifications. This layered approach to reviewing the survey enables you to pinpoint any significant security gaps swiftly. Once identified, these issues can be flagged for further action and incorporated into the evaluation documentation that you are compiling.
Conducting an assessment is just one part of a TPSRM program. After identifying any potential security risks, it’s necessary to be actionable.
Within most organizations, business units and teams typically hold the mantle of risk ownership. This means that the responsibility of evaluating the security of third-party vendors may rest with the information security team, but the power to make final decisions lies elsewhere. The role of the security team then evolves to one of an advisor, providing insights, expertise, and recommendations to enable business units to make well-informed decisions. By leveraging the findings from your assessments, it is vital to clearly communicate the significance of any gaps and their potential impact, thus equipping decision-makers with the knowledge required to take ownership of their choices. Collaborating with specific stakeholders, such as data stewards who may have regulatory authority, becomes part of this process, ensuring that procurement decisions align with the organization’s compliance and security standards. Furthermore, offering alternative solutions or contingency plans is essential, particularly when preferred vendors may not meet established security criteria.
When an organization opts to engage with a third-party vendor whose offerings fall short of the minimum security requirements, it is imperative to document and manage these risks and exceptions diligently. A central risk register is instrumental in maintaining visibility and accountability, enabling the organization to respond proactively should any risks materialize. This approach not only tracks the risks but also cultivates risk awareness and accountability across the enterprise, fostering a robust information security culture.
Isora facilitates this process by allowing for the seamless tracking of risks and exceptions noted during the assessment. Assigning these risks to the appropriate individuals and business units within the organization, along with details such as risk treatment, priority, category, impact, likelihood, and relevant metadata, is streamlined within the platform.
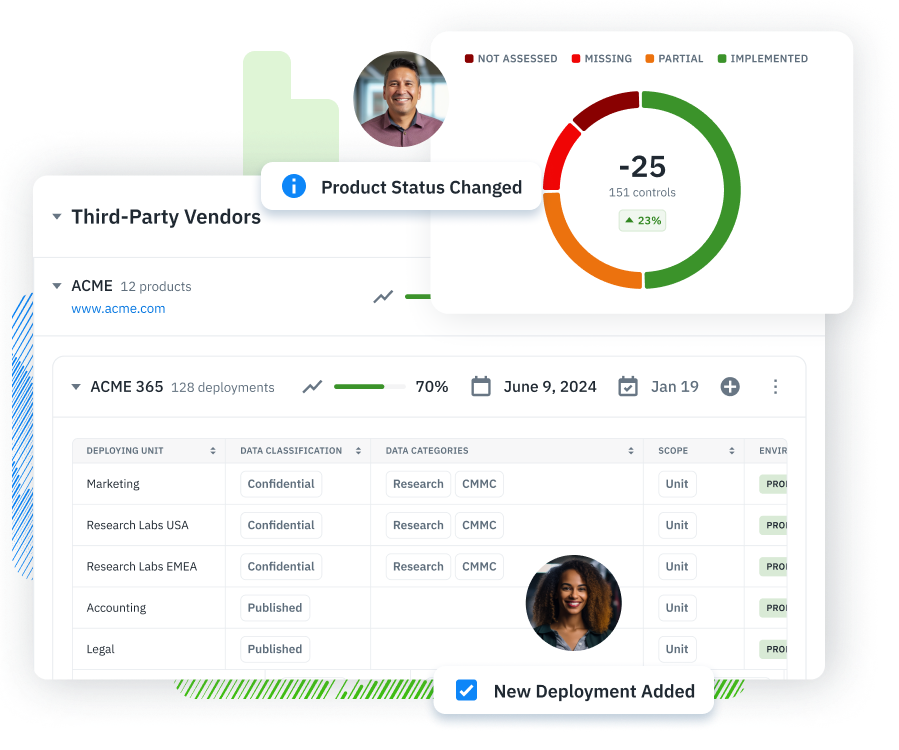
Maintaining a comprehensive inventory of third-party vendors is a recommended practice within TPSRM programs. This inventory acts as a reliable record of all vendor relationships, assessments conducted, contact information, ownership details, deployment data, data classifications, and other pertinent metadata. Such an inventory is not only critical for audit and regulatory compliance but is also invaluable in managing the response to supply chain attacks. Understanding the deployment scope of third-party products, the data or systems they interact with, and the responsible parties is crucial in the event of a cyberattack.
Isora’s inventory management feature provides a centralized and intuitive platform for managing vendors and their offerings across your organization. It offers a holistic view of all vendor-related information, including historical assessments and associated documentation.
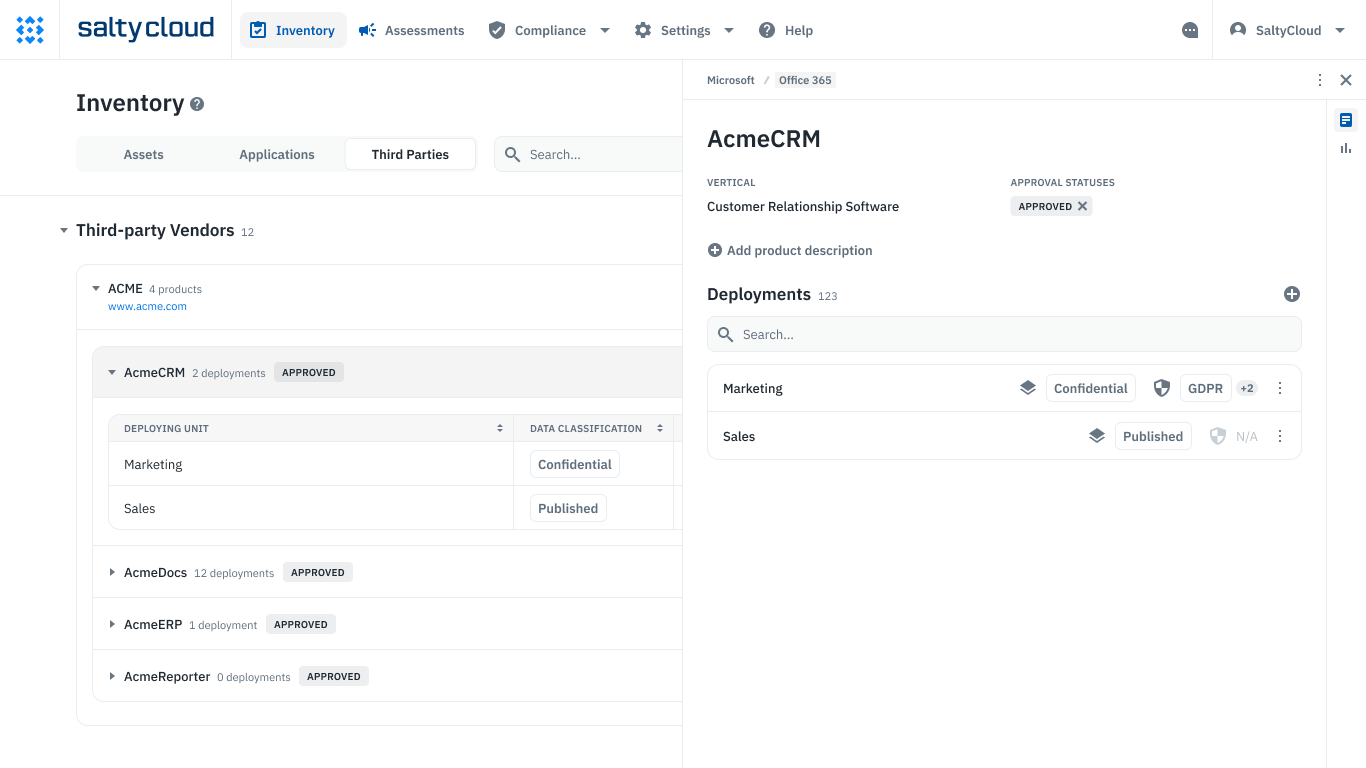
The third-party inventory section of Isora.
Lastly, third-party security risk assessments should not be viewed as a one-off activity. Continuous monitoring is essential, and this entails regular reassessment of vendors and the utilization of risk intelligence tools to automate the tracking of emerging threats. By embracing a cyclical approach to vendor assessment, organizations can stay ahead of new risks and ensure that their third-party risk management remains dynamic and effective.
Just as organizations depend on third-party vendors for essential services, they must also place importance on the thorough execution of third-party security risk assessments. This guide has provided a structured approach, offering clarity at each stage—from planning to evaluation. Isora GRC plays a crucial role in streamline the complexity of this process to manage these assessments. It equips your organization with the ability to confidently oversee, mitigate, and respond to the risks associated with third-party relationships, ensuring a robust and proactive third-party security risk management strategy.